Why do employees not care about cyber security?
Human behaviour plays a pivotal role in cybersecurity, heavily influenced by psychological factors and workplace culture. Stress, cognitive overload, and lack of motivation can lead to poor security practices. Employees under high stress or facing unrealistic expectations are more likely to make errors such as clicking on phishing links, using weak passwords, or neglecting security updates. Toxic workplace cultures, where employees feel undervalued or overworked, can exacerbate these behaviours, leading to a heightened risk of security breaches. I have been impacted by inadequate leadership, which caused a drop in morale, burnout and a total lack of ownership.
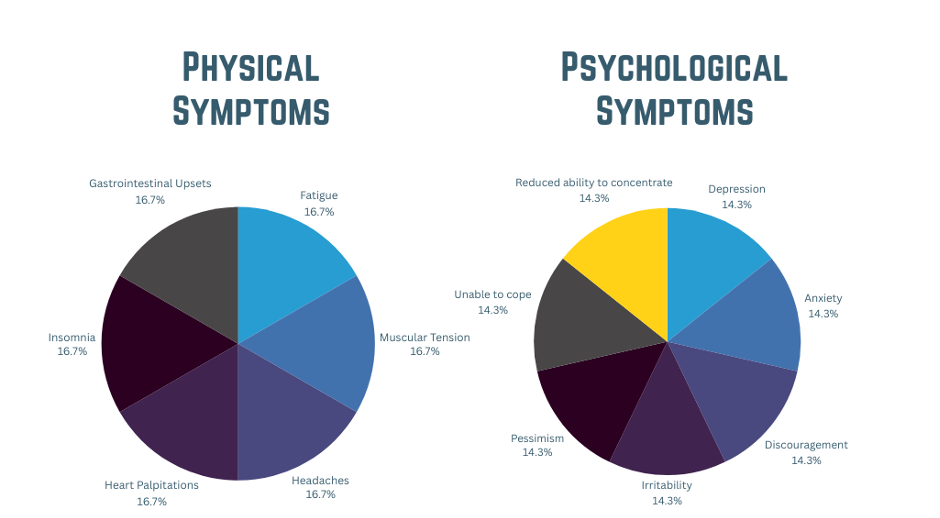
When employees experience high-stress levels, it affects their ability to perform their everyday tasks and overall communication, along with security protocols. According to the research conducted by the Victorian Department of Health, the symptoms can vary from physical and psychological to behavioural. Below is the chart with all the symptoms an employee may experience.
For instance, an overworked employee might feel frustrated with a newly introduced security protocol on top of an already big and tiresome workload. An employee may think that since the organisation is not taking care of the employee, then the employee doesn’t have to work as hard or comply with the security measures. This not only compromises the organization’s security but also affects overall productivity and morale.
Addressing these issues requires a holistic improvement plan that prioritizes employee well-being and fosters a positive security culture. Implementing regular mental health check-ins and providing resources to manage stress can help reduce the cognitive load on employees. There are many resources available to help employees, however, if the leaders of the organisation are not involved or are not nurturing a collaborative environment, regardless of the available tools, nothing will work. It is the role of the leadership to establish clear, achievable security policies and provide comprehensive training. It is essential to empower employees to follow best practices and promote a culture of appreciation and recognition. Encouraging open communication and feedback can also help in identifying and addressing stressors and security concerns proactively.
Active workforce involvement is crucial for creating a secure environment. Employees should be encouraged to participate in the development and refinement of security protocols, ensuring they are practical and user-friendly. Creating a network of security ambassadors or champions within teams can help disseminate information and foster a culture of vigilance. Regular town halls or feedback sessions can provide platforms for employees to voice concerns and suggest improvements. This participatory approach can lead to greater buy-in and adherence to security measures, as employees feel valued and heard.
In one of the organisations where I worked, compliance was at the forefront of the organisation, encouraged and emphasised by the leadership. At the beginning of my journey with this organisation, I spent 2 weeks ensuring that I had a solid understanding of all the compliances: from HR to IT and Security. I have completed hours of readings, videos, and multiple-choice tests before being allowed to be on the tools. It was ingrained in my brain to act with vigilance and a strong understanding of the company’s values. A positive culture, daily catch-ups with the leadership, non-hierarchical structure of the organisation and overall enabling environment created a fantastic workplace. Everyone wanted to do their best and everyone wanted to make sure that their teammate, regardless of the department, was feeling supported, encouraged and cared for. This kind of environment may be hard to create, but it is not impossible.
Several challenges arise when addressing the human aspect of cybersecurity, especially in toxic work environments. One major challenge is changing established negative behaviours and attitudes. Overcoming this requires consistent effort and leadership commitment to fostering a positive culture. Providing training that emphasizes the importance of mental health and well-being can help shift mindsets. Another challenge is ensuring that security measures are not perceived as additional burdens. Simplifying security protocols and integrating them into daily routines can make compliance easier and less stressful.
To evaluate the effectiveness of the improvement plan, organizations can use a range of metrics. Employee engagement surveys can provide insights into morale and perceptions of the workplace culture. Monitoring the number of reported security incidents and compliance rates with security policies can indicate the effectiveness of training and awareness programs. Metrics such as the frequency of password changes and participation in security training sessions can also provide valuable data. Regularly reviewing these metrics can help organizations identify areas for further improvement and ensure that their security strategies remain aligned with employee well-being.
In conclusion, the human aspect of cybersecurity is deeply intertwined with psychological factors and workplace culture. By addressing the behavioural impacts of stress and toxic environments, organizations can significantly enhance their security posture. Developing a holistic improvement plan that includes mental health support, clear communication, and employee involvement is essential. Recommendations include investing in employee well-being programs, fostering a positive security culture, and regularly evaluating the effectiveness of these initiatives. By prioritizing the psychological and cultural aspects, organizations can create a more secure and resilient environment.