Thanks to Matthew Mansour
Lecturer | IT Consultant for SMEs | IT Auditor
… and Thanks to TAFE for this eye-opening scholarship.
In this report, NMX digital consultancy is presented with an opportunity to provide company “X” with a cybersecurity framework. NMX will help X establish an educational framework with an emphasis on a human-centric approach for both organisations and foster an environment of professional and personal responsibility.
Both entities, NMX and X, are independently owned companies that work together on a variety of projects. NMX is an independent marketing consultancy, offering tailored customer-centric digital solutions. X is an independent brokerage company assisting clients with contractual risk management and mitigation. Both companies are at the start-up stage, however, X works with enterprise-level companies. On the other hand, NMX is at the beginning of its start-up journey and has the knowledge to help X comply with ever-growing cyber risks. X, as a more established start-up, has the capital to outsource operational business tasks such as accounting, IT management and marketing. X relies on its IT provider, Jupiter Group, for ensuring security via Microsoft 365 and Microsoft Azure. Despite a robust security architecture provided by Jupiter Group and Microsoft, the X team is lacking cybersecurity awareness, making X the perfect target for cyberattacks.

As mentioned earlier, both companies are at the very early stages of development and while X has the capital to implement strong security practices, the company is lacking the understanding of the importance of this subject. The job of NMX is to educate, collaborate and implement a seamless approach to cybersecurity that would come as second nature to X employees. NMX’s focus is to educate X leadership and employees about the crucial significance of cybersecurity in their organisation. Due to the small team size, the process won’t be as strenuous, however, due to a high focus on the revenue-generating activities by all team members, the security questions are subjugated to a minimal priority. The integral message that needs to be delivered to X is that the [c]ore to creating an effective cyber security culture is recognising that people make an organisation secure, not technology by Everard, T. (n.d.). What is Cyber Security Culture and why does it matter for your…. [online] PA Consulting. Available at: https://www.paconsulting.com/insights/what-is-cyber-security-culture-and-why-does-it-matter-for-your-organisation.
To make the educational material as relatable as possible, we will be considering the way our brains process and memorise information. According to Matthew Oterbridge, there are many ways our brains retain and recall information (MATTHEW OUTERBRIDGE. (n.d.). Learning How to Learn: An Infographic. [online] Available at: https://www.outerbridge.blog/articles/learning-how-to-learn-infographic.) and to accommodate all learning styles, we will implement a 5-way information presentation. The primary focus for NMX is to ensure that by the end of the course, the managing director and his right hand are acting as leaders in cybersecurity excellence and lead by their example on how to mitigate and navigate the murky waters of cyber threats. The members will receive the information via video recordings followed by a short test, pdf with infographics summarising the video content, the news and articles about “breaking” cybersecurity news and articles that would inspire lunchtime conversations. At the end of each module, the team members will be required to complete a short test.
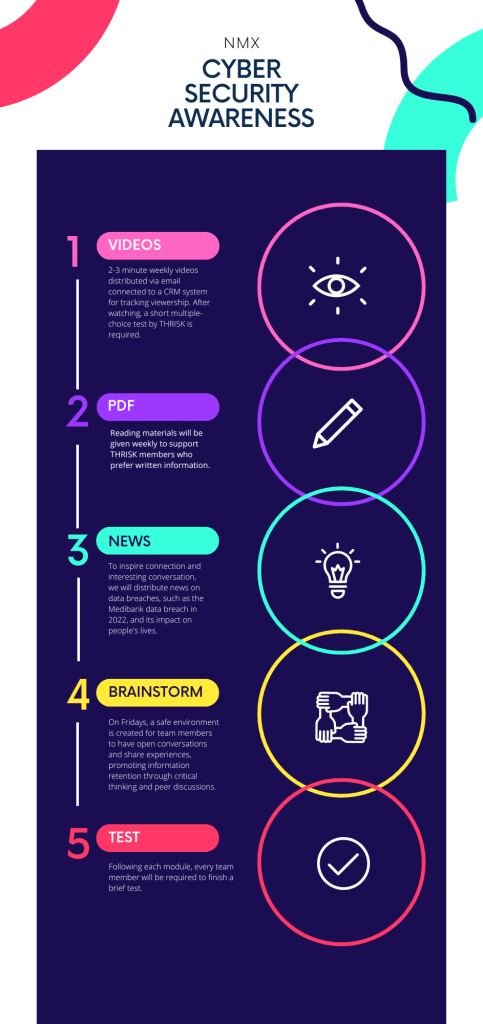
The above covers the general framework and information presentation types. Most importantly, NMX will be constantly evaluating the engagement, reporting activity, and general attitude of the team and running Q&A assessments.
Timeline and schedule
- Timeline
- Week 1: Audit and compliance check + Leadership Commitment
- Identification of the core issues, and collection of all necessary information from the IT department, marketing, finance and other departments.
- Introduction to the BASICS of CYBERSECURITY
- Why do we care? What are the implications? Who is at risk?
- Share the cyber news (industry-specific or personal)
- www.brokernews.com.au. (n.d.). Brokers warned: Prepare for cyber threats. [online] Available at: https://www.brokernews.com.au/news/breaking-news/brokers-warned-prepare-for-cyber-threats-284503.aspx [Accessed 11 Jul. 2024].
- Share the cyber news (industry-specific or personal)
- Why do we care? What are the implications? Who is at risk?
- Policy Review
- Week 1: Audit and compliance check + Leadership Commitment
- Week 2: Incident Response Plan Implementation
- Initial incident response plan implementation
- Access controls and monitoring
- 1-5 NMX framework
- Assessment: ensuring that everyone in the team has the same level of understanding
- Policy review edits to improve the
- module and implement new standards and compliances.
- Ensuring all departments are aligned and understand the new approach.
- Week 4: Training Assessment and Employee Feedback
- Testing, revising and reviewing the effectiveness of the new compliance and identifying any possible issues.
- Collecting testimonials for a deeper analysis and recognizing any knowledge gaps
- Including Cyber Security in the employee’s KPIs from the next module
- Initial incident response plan implementation
1-week break for evaluation and study break.
- Week 5-8: Rinse and Repeat
- Repeat of Week 1-4 tasks based on the identified gaps or any additionally identified threats.
1-week break for evaluation and study break.
- Week 9-12: Cement & Concrete
- To avoid complacency, shift the responsibility for the next 4 weeks’ topic choice to the “influencer” of the team (preliminarily agreed with the MD)
- The topics will be written in advance based on the latest evaluation.
- Nominate a team leader who will be responsible for all cyber questions and empower the person with all available tools and information.
- Provide the team leader with the tools and resources to help further the implementation of a cyber-safe culture.
- Update the policy and update the incident response plan.
- To avoid complacency, shift the responsibility for the next 4 weeks’ topic choice to the “influencer” of the team (preliminarily agreed with the MD)
Final touch, at the end of our course, the members will receive stickers to put on their laptops or screens. It will make the members not only remember the course but can also invite conversations with new hires, clients and potential prospects.

NMX digital consultancy will continue supporting X providing undivided attention through partnership as the digital space continues developing, shifting and changing. NMX strongly recommend revisiting the security standards every 6-9 months to ensure that everyone in the team is aligned with the latest updates and changes in the cyber security space. The entire course is dedicated to being customized, re-evaluated and re-adjusted to the necessary curriculum to encourage the team members to cultivate a deep understanding of cyber security and nurture a culture of personal responsibility in a professional setting. As X continues its growth, the requirements will change and the need for shared responsibility and accountability. It’s NMX’s long-term commitment to keep X informed, educated and protected.
